Contents
The problem
You like to sniff your firewall. The problem is that the firewall is (of course) a headless linux box without a gui. After half of an hour you’ll get headache from starring at the characters fly bye the screen and you really wish you could look at the beauty of whireshark. This document is going to tell you how this dream could get reality 🙂
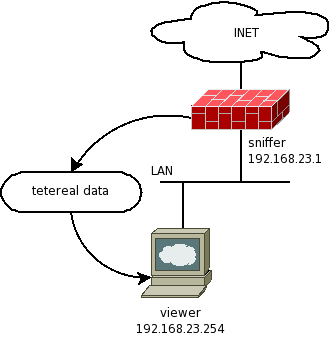
Below is the basic setup:
The tools
- To transport the data from our sniffing box we will use the “TCP/IP Swiss Army Knife” netcat. You can get it from here but it is installed with most *ux distributions.
- And of course wireshark (formerly ethereal).
The solution
Start the netcat listener
First you have to start a netcat listener on the viewer host.
On linux you have to use the while-loop (hard-listening) because otherways the listener will die if the connection gets interupted. The WIN32 version has the -L flag to archive this.
One other thing is that with the GUI version of ethereal you have to use a little trick, since it does not seem to read from stdin; but it can read from pipes. So you have to create a FIFO pipe first where the netcat listener can write to:
1 2 3 | ### viewer ### mkfifo ~/mypipe while (true); do nc -l 192.168.24.254 4711 >> ~/mypipe; done |
Start wireshark
Then we have to start wireshark. Then go to Capture->Options and write the name of your FIFO-pipe into the “Interface” field. Don’t select “Capture packets in promiscuous mode” since we define these things on the sniffer host!
Start the sniffing on the sniffer host
1 2 | ### sniffer ### tethereal -l -F libpcap -w - not port 4711 and not port 22 | nc 192.168.24.254 4711 |
Happy sniffing!!!
Todo
- Try the netcat in UDP-mode. Wireshark crashes after a view packages with the UDP mode. Don’t know the reason nor the solution
- Encrypt the sniffed traffic. This should be easy with cryptcat.
- Find a more stable solution. Sometime it doesn’t really work. It doesn’t work if the steps get out of the right order.